In an era dominated by digital communication, the incessant barrage of spam emails has become a ubiquitous nuisance, infiltrating our inboxes and inundating us with unsolicited messages. As a response to this escalating problem, a growing number of users are turning to disposable email addresses as the ultimate defense against spam. These temporary, one-time-use email accounts serve as a virtual shield, protecting users from the constant onslaught of promotional messages, phishing attempts, and other unwanted communications. The concept of disposable email addresses is not entirely new, but its popularity has surged in recent years as individuals seek innovative ways to reclaim control over their inboxes. Disposable email services provide users with a unique and temporary email address that can be discarded after a specific period or usage. This not only shields users from the relentless waves of spam but also safeguards their primary email addresses from falling into the hands of unscrupulous marketers or cybercriminals. One of the primary advantages of disposable email addresses is their effectiveness in preventing the accumulation of spam in a user’s primary inbox.

By utilizing a temporary email address for online registrations, newsletter subscriptions, or other non-critical activities, users can easily segregate and filter out spam from their primary email accounts. This proactive approach not only declutter inboxes but also enhances the overall email experience, allowing users to focus on essential communication without the distraction of unwanted messages. Furthermore, disposable email addresses serve as a powerful tool in the fight against phishing attacks. Phishing, a malicious tactic employed by cybercriminals to trick individuals into revealing sensitive information, often relies on emails designed to appear legitimate. By using disposable email addresses for online interactions that may carry a higher risk of phishing attempts, users can minimize the potential damage of falling victim to these deceptive tactics. The disposable nature of these email accounts ensures that even if a phishing attempt is successful, the compromised email address is of little value beyond its initial purpose.
While the rise of disposable email addresses provides users with a valuable defense against spam, it also raises concerns about the sustainability and environmental impact of creating countless temporary accounts in block disposable email addresses. As individuals increasingly adopt disposable email practices, there is a need for responsible usage and consideration of the broader environmental consequences. Balancing the convenience of disposable email addresses with the environmental impact highlights the importance of mindful and sustainable digital practices. In conclusion, the surge in popularity of disposable email addresses marks a paradigm shift in how users approach email communication in the digital age. As the ultimate spam defense, these temporary email accounts empower users to take control of their inboxes, mitigate the risks of phishing attacks, and enhance their overall online experience. However, it is crucial for individuals to use disposable email addresses responsibly, mindful of the potential environmental repercussions, as we navigate the delicate balance between convenience and sustainability in the digital landscape.
Administrating a specific organization can be debilitating on the off chance that the staff depend entirely on their manual capacities Since overseeing an organization is made conceivable due to cutting edge PC programming, the executives has become more complex these days as increasingly more programming is created. In view of the series of progression, managing expands the quantity of cycles which are robotized. Two of the computerized processes done in organization are network design and organization examination. Network design is a robotized cycle which gives various advantages in network organization. It can diminish how much time assigned for specific errands and lessen the quantity of blunders that might perhaps be committed in any undertakings. It can likewise improve and increment design consistency in numerous different organized frameworks.

Besides, it presents a specific approach to reporting process. There are various setup apparatuses accessible in the market these days. Most apparatuses do have specific elements that cannot be tracked down in different devices. Respectable organizations offer organization design devices that can store and track waiters, switches, and switch arrangements. Merchants offer apparatuses that can oversee numerous gadgets in a productive manner. These are only a couple of the organizations that sell network setup items. Then again, an analyzer is a PC programming or equipment that can hold up bundles that streams in an organization to have every one of them decoded and examined in view of specific determinations. Network analyzer is otherwise called convention analyzer, parcel analyzer, or sniffer. An analyzer can hold up traffic on some other regions relying upon whether the LAN utilized is wired or remote.
Wired LANs really do have the capacity to catch parcels at any pieces of the organization. Nonetheless, on remote LANs, traffic can be held up just through a specific channel. There are various programming programs for network examination. The top programming incorporates flesh eater, sniff, Eternal, Fluke Lamenter, Microsoft Network Monitor, among others. These products are top of the line in the market since their elements incorporate their capacity to recognize network issues, distinguish interruptions in the organization, gather and present organization measurements, to give some examples. There are a few sellers of organization analyzers. The product can cost cash, nonetheless, there are programming that can be gotten for nothing. The sd-wan providers web has various locales that offer both free and paid programming. It is vital to peruse audits of every item before you select one so you can purchase the best programming in the market today.
Online screen share recorders assist you with recording anything you are doing on your PC screen share. Yet, the inquiry is how might they help you, where could you at any point get them and how might you utilize them this is the very thing we will make sense of in this article. Along these lines, how about we come to the heart of the matter without killing any additional time. As said before, a screen share recorder, very much like some other application you can download from the Web, is an application. Each application is created with the expectation to address the issues of end clients. A few applications are intended to be utilized by selective clients, for example, applications created for NASA. Then again, some applications are produced for the overall population to utilize.
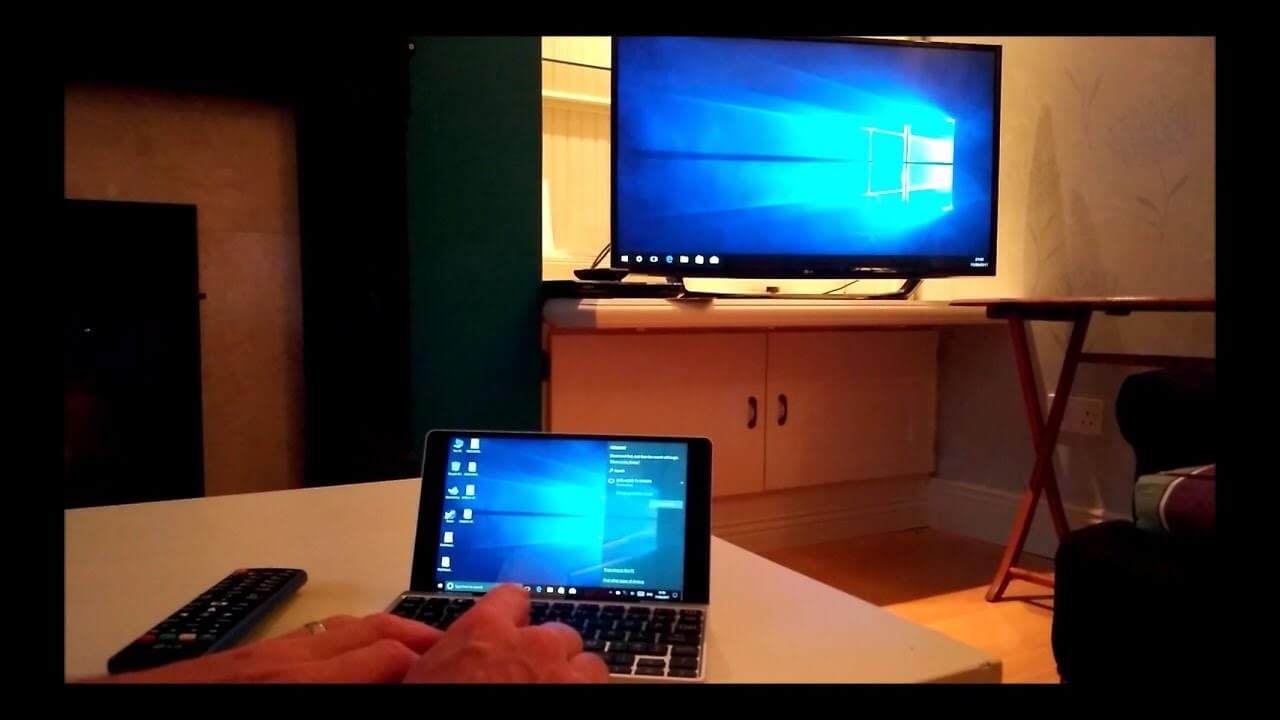
And that implies anybody all over the planet with admittance to the Web can download these applications by paying a couple of bucks and introducing them on their PC.A few applications are paid while others are free. This is valid for online screen share recorders also. Allow us first to investigate these applications. A screen share recorder or screen share catch application permits you to take pictures or video of your PC screen share. Maybe you are holding a camera and taking photographs or video of your screen share. In fact, lg screen share not working can utilize your camera to record what you are doing on your PC, yet that will not be exceptionally advantageous. A simple way is to utilize an application to do a similar work. You should simply send off the recording application and hit the record currently button.
The screen share catch application will then begin recoding your exercises. After you are done, it will save the video or pictures. You can then change over the recordings into your ideal arrangement, like MP4, 3gp a perfect world; you might need to save the video in MP4 design, which is the organization that is viable with cell phones. The recordings you recorded can be instructional exercises to show others on the web how to follow through with something. For example, assuming that you are a web designer, you can make instructional exercises about how an amateur can make a site without any preparation. You should simply make a straightforward site on your PC while recording the whole strategy with the screen share recorder. You can then impart these caught recordings to the whole world through your own site or through a video sharing site, like YouTube.
The world is quick changing and Business companies everywhere throughout the world are finding a way to take their association to a totally unique level. They are not dithering to utilize different strategies like broadening the scope of their intended interest groups by connecting with them regardless of whether they are in various nations, redistributing their work which unquestionably gives low operational expenses also a lot of time for organizations to concentrate on their center business. For those organizations which are extending their base and making their quality felt in various pieces of the globe numerous an issues appears to emerge. They may make some intense memories holding their objective buyers or monitoring their workers. The principal explanation for a firm not prevailing in their needs is a correspondence hole among them and their customers. As correspondence is the fundamental extension between a customer and a firm and the firm and achievement organizations can not rest expecting that everything will be okay as time recuperates everything.

A VPN is a private PC organize that is situated in an overlay on a current system and utilizations an open system for example, the web to make a private, secure correspondence scope or to interface remote locales or clients together. It fills much need for example, giving secure expansion of a private system into web which is normally shaky and inclined to assault, utilizing a virtual association rather than a genuine association for example and a rented line. It tends to be a remote access or a site to site arrange. In any case in either case we need explicit programming and equipment to manufacture a VPN. For example, we need programming for remote client, devoted equipment, free proxy server my review here to be utilized by the specialist organization, secure PIX firewall and so forth and equipment like SEP modules. VPN enhanced switches and so on.
Making advances on the upsides of a VPN or the manners by which it can profit a business to succeed, VPN are a practical medium which spares the organization an enormous entirety, they are portable and give security to its clients which builds customer’s trust in the organization, it gives a huge topographical availability which empowers the representatives to sign in at places agreeable to them in this way expanding network, they additionally offer broadband systems administration, remote worker support and so on. For similarity reasons most Cisco systems use Cisco VPN programming, however never the less regardless of whichever VPN customer utilized, Secure Sockets Layer ought to be set up for greatest productivity and ought to contain legitimate safety efforts to abstain from hacking of individual information of the customer.
Your nearest companion would consistently protect you and never let you down. The identical should be stated of your own computers. In this era, the typical individual needs 28 computers. You need computers to your lender, email, casual organization, debts, and some other internet based asking balances. Now you genuinely stand up the computers for a variety of logins on the job. It can get shocking to remember all of the computers that you use at a day’s time. It is enticing to use similar key for all of the locales and documents you ought to get to. But this is setting up you to have your key important STOLEN. Furthermore, the outcomes of getting your solitary keyword hacked can be dreadful. Consider precisely how much a keyword guarantees. Internet based banking and investment capital. Your keyword remains between your money and a criminal.
Email accounts. Your keyword protects your messages from being hacked. In the event you have online bills and bank articulation, the hoodlum may get into your document data. Online shopping Your Visa amount along with other personal data are viewed by Social account hacker. Furthermore, these are only your Private Accounts. Below are a few substantial tips to use in the creation of your computers. Toss your key word commitment from the window. Studies reveal that 1/3 of all Americans who use a PC use a similar keyword for every website. In case a cheat gets your key and hacks to your email, he had then have the ability to access some documents he finds. He could really tidy out you and stand up enormous obligation within a concise timeframe. Applying only 1 key word for the entirety of your documents hands the cheat a open greeting into the entirety of your documents and information
Easier is not better. A decent little people really use their debut to the entire world, their children’s titles, as well as 12345 as their own computers. Such computers require developers only seconds to divide. Straightforward computers leave your documents open and expecting that offenders will exploit. You need to leave your money lying around your entryway patio and try on Red Teaming. Keep it at the noggin. Irrespective of whether people have more than 1 secret key they often record them and render them from the PC, below their games console, in their program, or keep them inside their mobile phones. This basically blessing wraps them to get a criminal. When he scores that the key rundown, its bye money and hello deceptive fees blend this up. Computers which simply contain letters are not anything but hard to observe or concept, especially in the event they are only lower case.
Some are limited, unassuming, and some are even free. What should be kept an eye out for while looking at an Ecommerce hosting plan is, will the strategy fit your necessities. Gigantic affiliation or insignificant one, free blueprint or extravagant one, what is critical the most is cleared out the game-plan is helpful for you.
Costs
The value go after plans will change in any case on the off chance that you are an exclusive business or a person with not a lot of necessities than there are unassuming reasonable and solid web working with an offshoot plans. What is basic is to explore the designs to check whether they make a solid match. Different plans that are more moderate do not have the data move breaking point or space that an even more extravagant game-plan will have. Everything relies on the extent of online business that you will do with the website.
Windows and Linux
Internet business hosting plans are accessible several choices particularly in the event that you are searching for a game-plan that has a colossal heap of transmission capacity and space. On the off chance that you are in this class there are in like way Linux member web working with plans. These two suppliers can oblige more noteworthy space and data bandwidths with respect to an best ecommerce hosting plan. These two affiliations, windows and linux, have devoted subject matter experts and their client organization is in general very phenomenal. They regulate clients that do a lot of electronic business so you can be certain they are exceptionally secure as well.
Examination
You can explore on the Internet whenever you have pinpointed the necessities you need to address with your Ecommerce hosting. There are many working with plan associate objections that you can analyze as many will control you through the site showing their abilities in Ecommerce hosting plans. There are in like way get-togethers on the Internet where others can share how their encounters have been with various plans. An Ecommerce hosting plan is not hard to track down yet what is somewhat harder is discovering one for you. Examining various plans can improve on it discovering ones that are both moderate and solid.
Web Hosting is a run of the mill wonder now and all associations and individuals need their own locales to be seen by all. The assistance of Web working with is of different sorts and which type should be picked for your webpage should be picked by you as demonstrated by the necessities of your website. Pick simply the one that suits your necessities so it is more reasonable and supportive for you. Here are the various types of organizations available online these days.
Shared Hosting-As the name suggests, here you need to bestow your laborer to various clients moreover. In this sort of sharing, a site is worked with on a specialist who is shared by various customers who have their site on a comparable laborer. Upkeep of the specialist is totally the obligation of the host and they will ensure that the laborer is constantly running high. This assistance is by and large more affordable.
Submitted Hosting-This is a help where each and every customer is allotted an entire specialist without bestowing it to some different clients. The customer can in like manner have more than one site on this specialist. The paas platform as a service customer here is totally liable for managing his own site page. This is a more strong sort of working with that basic working with.
Free Hosting-Here the customer can have his site freed from cost by business controlled associations. This assistance is not for affiliations and business houses as they need a huge load of information support. Singular pages go with such a working with.
Web business Hosting – This paas help comes all out with a wide scope of online business gadgets and is expressly expected for coordinated business on the net. Thusly such a web working with is best when you need to have your webpage page to coordinate online business.
Stage base-The help also shifts as demonstrated by the stage. Windows web working with will maintain features the windows stage while Linux web working with will maintain the Linux stage. Most associations require SaaS joining for their present applications so they stay accessible in the cloud. Also, stage as a help courses of action like AWS help associations with getting a good deal in front of an audience costs. The association is tremendously improved and the customer getting costs are massively diminished. Most organizations offered by SaaS execution join a compensation all the more just as expenses emerge enrollment allowing model which help associations with orchestrating out their costs early.
GPS (Global Positioning System) has altogether improved our lives. It offers straightforwardness and handiness in route. In any case, since it depends on altogether innovation and development becoming the dominant focal point, GPS will even now be improved bit by bit. Despite the fact that GPS can focus in a genuinely precise area of a GPS transmitter, it may not give 100% exactness. It is important that we know how GPS functions so as to know its deficiencies and it favorable focuses.
![]()
What is a Global Positioning System?
Worldwide Positioning System is only a lot of satellites coursing the Earth and passes on explicit data about time and position, regularly delineated as far as longitude, scope and height. On an essential level, the GPS sets up four factors: longitude, scope, stature (height) notwithstanding time. At the point when a Global Positioning System collector is connected to a gadget, the GPS sets up the specific situation of that gadget. A normal of four satellites will be utilized to build up a situation in 3-D space.
The estimation is carried out by building up the sign exchange time including the purposes of observation and the four satellites gps vehicle tracker. The separation including a reconnaissance point and the satellite is built up by increasing the sign time to the speed of light. At the point when at least three satellites are utilized with each running its own PC calculations assists with setting up the exact situation of the gadget.
Employments of Global Positioning System
Information profited from the Global Positioning System could be utilized for a wide assortment of employments including, chasing, climbing, outdoors, reviewing, sailing, avionics, national security administration and general route purposes.
Disadvantages of Global Positioning System
The specific area is right inside a scope of 20 m to pretty much 1 mm. Accuracy can be self-absorbed by various considers, for example, mistakes separation estimations, harmed travel time estimation, signal communicate blunders (climatic interruption influences the signs) and beneficiary blunders.
Choosing the correct GPS Tracker for Vehicle
To choose the correct GPS tracker for vehicle, one needs to look for a system that benefits both vocal and graphical bearings. The GPS tracker systems that utilizes guide and screen incorporate bolts that represent the course of a turn alongside showing where your vehicle is on the guide in comparative with the goal one is going. Different systems utilize the head unit or radio to show the name of the road you are probably going to make a turn or which you are going towards. Both of these GPS trackers for vehicle systems additionally give verbal bearings as you gravitate toward a turn.
Quit referencing you will be away on vacations or broadened leave. Do you by and by know everyone on your companions list getting it is No. By expressing on your status or giving dates when you will be away from home or the workplace is welcoming individuals to snoop around your premises. Quest Google for thefts and burglaries while clients twittered and refreshed their status to Away from home as of late law requirement prompted Facebook clients to reconsider what they place into their status fields for Facebook and Twitter A tip consider refreshing your companions after you come back from occasions and attempt to downplay dates and times.

Prevent Google from ordering your Facebook Profile
Prevent web indexes from finding and ordering your profile. Quest for your name in Google and chances are your Facebook profile will show in the list items. Do you need the 5 ways to hack a facebook account entire world to discover you on Facebook to prevent outsiders from getting to your profile alongside spam companion welcomes evacuate this posting by visiting your protection settings To incapacitate this element, go to Account > Privacy Settings > Search > Open Search results > Remove tick in box in the wake of impairing this capacity, Google will expel your posting inside 1 – 5 weeks. Specific time period for web search tool expulsion at present obscure.
Quit utilizing Facebook applications with share data to outsider locales. Farmville and Mafia Wars are not by any means the only applications found on Facebook There are a huge number of Facebook applications which can be downloading and utilized on Facebook and on your site. Shield yourself from these applications and your companions applications by visiting Account > Privacy Settings > Application and Web Sites. From here you can control what companions share about you on Facebook. It additionally controls what applications can use from your profile when you introduce on your profile or site. Moment Personalization Pilot Program is when site picked by Facebook can tweak their site with the data from your profile. Unpick to expel this element. Informed the page a couple of times and got disregarded, presented on the divider and got prohibited, and after not got notification from Facebook bolster essentially yielded annihilation. Anyway before surrendered thought talk in a language we as a whole comprehend: